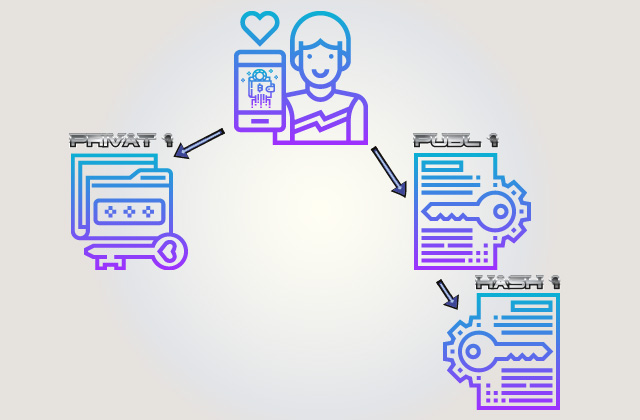
In life, we often have to sign ‘important personal documents’ (a kind of transaction) with our private key in order to transfer money to third parties. The public key serves to verify the authenticity of other people’s transactions.
Table of Contents
Hash function
The hashing operation is quite easy to explain. Take random numbers, for example: 3+5+4+6+7+8+9+11+13+16+30+19+26. Add all the numbers together several times: 3+5+4+6+7+8+9+11+13+16+30+19+26=157 => 1+5+7=13 => 1+3=4.
This allows you to assign a unique number to any string. The addition procedure is called hashing, and the method itself is called a hash function. The unique number 4 obtained as a result of the addition is called the hash sum. A hash function can be represented as a meat grinder, into which a large piece of meat is placed, and mincemeat is obtained as a result. The reverse operation is impossible.
Properties of hashing:
- It’s impossible to determine the original sequence of numbers based on the result of adding the numbers together
- It’s impossible to select a sequence of numbers that will produce a predetermined result
- The slightest rearrangement of numbers in the sequence significantly alters the hash.
Public key hash
Bitcoin uses the hash sum of a public key as the address for cryptocurrency transactions. You can safely publish your bitcoin address in plain text. However, even decryptors won’t be able to determine the original key from the hash. The life cycle of the keys will end as soon as the transfer of ownership takes place. They won’t appear again in the future.
PRIVAT 1 is a private key.
HASH 1, or PUBL 1, is hash sum of a public key, i.e. bitcoin address.
HASH 2, or PUBL 2, is hash of a public key of the next buyer.
Property transaction
Let’s say there is a yacht owner whose ownership is not in doubt. On the market, the owner shows buyers the hash of his/her public key and the yacht number from the shipbuilding company, and everyone accepts this. Until the final sale of the yacht, the seller’s public and private keys are hidden from everyone. Buyers only know the hash sum of the public key and the corresponding yacht number.
When the yacht owner decides to sell it to a potential customer, they will create an advertisement in which they will write the yacht number and the hash sum of the yacht buyer’s public key. In other words, the seller signs the contract with his/her private key, attaching the public key.
After the yacht sale transaction, the private key will no longer work. There will be no second such transaction. Nothing is known about the buyer except for the public key hash until they sell the ownership of the yacht to the next buyer. This chain can be unlimited. By signing the yacht sale contract with a digital signature, the owner confirms their right and assumes the obligation to transfer ownership.
It is supposed that the personal key performs its privacy function only once and sends the change from the sale to his secret address. Therefore, it is difficult to determine how much cryptocurrency is located at the wallet address. The overall picture of the transactions is established due to the long chain.


 Telegram
Telegram