One of the main questions that interests the owners of crypto exchanges is how to make the exchange work as safe as possible. Exchange security consists of two critical components: the reliability of the exchange software and the security of the server infrastructure.
OpenCEX was designed with high security requirements in mind, and the code and dependencies are constantly being updated. In this overview, we have collected some practical tips on how to secure your server.
First, let’s look at the 3 main attack vectors that attackers can use:
- Distributed Denial of Service (DDoS) attacks. These attacks aim to overwhelm a web server with a massive amount of traffic, rendering it unresponsive and inaccessible to legitimate users.
- Brute-force attacks. Attackers use automated tools to try numerous username and password combinations in an attempt to gain unauthorised access to the web server or associated applications.
- Exploiting known vulnerabilities. Attackers exploit unpatched software vulnerabilities to gain unauthorised access to a web server or execute malicious code.
The most critical type of attack is one that gives the attacker full, root access to the server. This makes it possible to make any changes to the OpenCEX code, including replacing cold addresses for accumulating cryptocurrency. Under no circumstances should this be allowed.
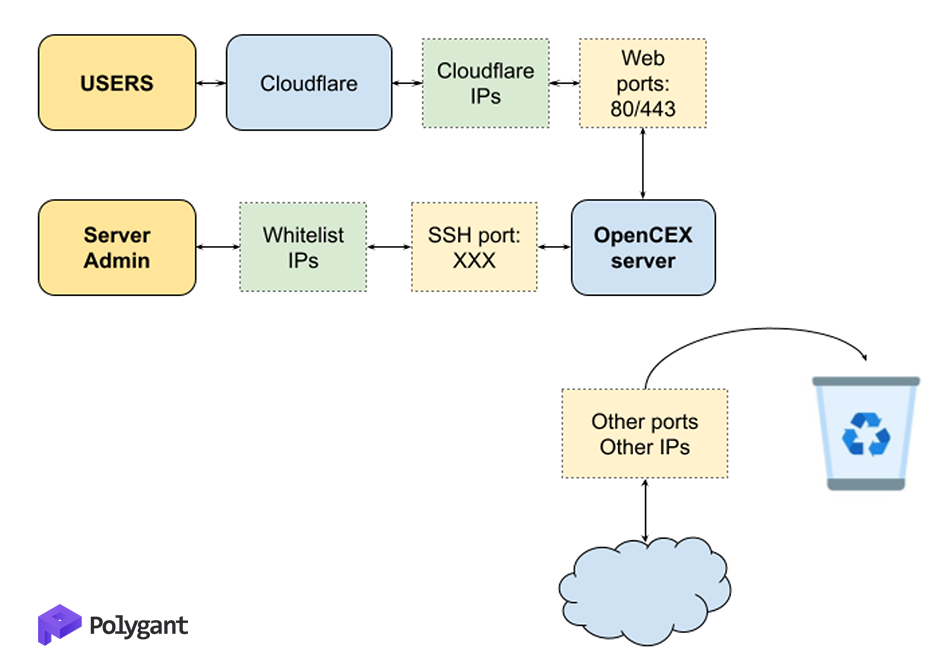
Simple tips to protect your server
- Be sure to use a reverse proxy service like Cloudflare. This will protect your server from DDoS and bot attacks, as well as hide the real IP address of the server. It’s IMPORTANT to immediately delegate the domain to the Cloudflare NS (name server), otherwise the real IP of the server may be compromised and attackers could try to bypass the protection.
- On the server firewall, disable external connections to all ports except 80/443 + the port you connect to via SSH. 80/443 port connection should only be allowed from the reverse proxy IP list (for Cloudflare see https://www.cloudflare.com/ips/).
- Don’t use the default SSH port. It’s better to change it immediately.
- Use a white list of IP addresses that are allowed to access the server on ports other than 80/443. This SIGNIFICANTLY improves security and makes it harder for attackers to do their job.
- Set up monitoring and auditing systems to track suspicious activities and changes on your server. You should also monitor checksums of critical services such as SSHd. Regularly review log files for anomalies and suspicious access attempts.
- Disable direct connection for root. Use su / sudo.
- Use the key for SSH access. If you still want to use password access, then use strong passwords. The difficulty of brute forcing a password increases exponentially with each additional character.
- Update server software regularly. Vulnerabilities are often found in popular software, sometimes critical ones, and it is very important to fix them in a timely manner.
- Regularly create backups of all important data on your server. This will allow you to recover data quickly in case of an attack or system failure.